Azure Hybrid DNS Part 2
Since the my first post about Azure Hybrid DNS, I ran into a few more scenarios that I want to share with you.
In this post, I will go over the scenario in which you can use Azure Private DNS Zones as a sub-domain of your locally hosted DNS Zones.
Table of Contents
This is a multi part article with the following parts:
Part 1 - Azure Hybrid DNS Architecture
Part 2 - Azure Hybrid DNS Part 2
Introduction
You might be wondering, why would you want to use Azure Private DNS Zones as a sub-domain of your local DNS zones in the first place and I would not object. But during migrations and transformation processes, you don’t always know what will come up.
If its possible for you to use your local DNS zones for automation processes, great, you should not hesitate to use them 😉
However, there are certain scenarios in which you for instance shift workloads to the cloud and the simple management of DNS records is not that easy. There might be ITSM approval processes in place or the service is bought and managed by a provider whom does not let you manage records, what ever the case might be.
Goal
What do we want to achieve?
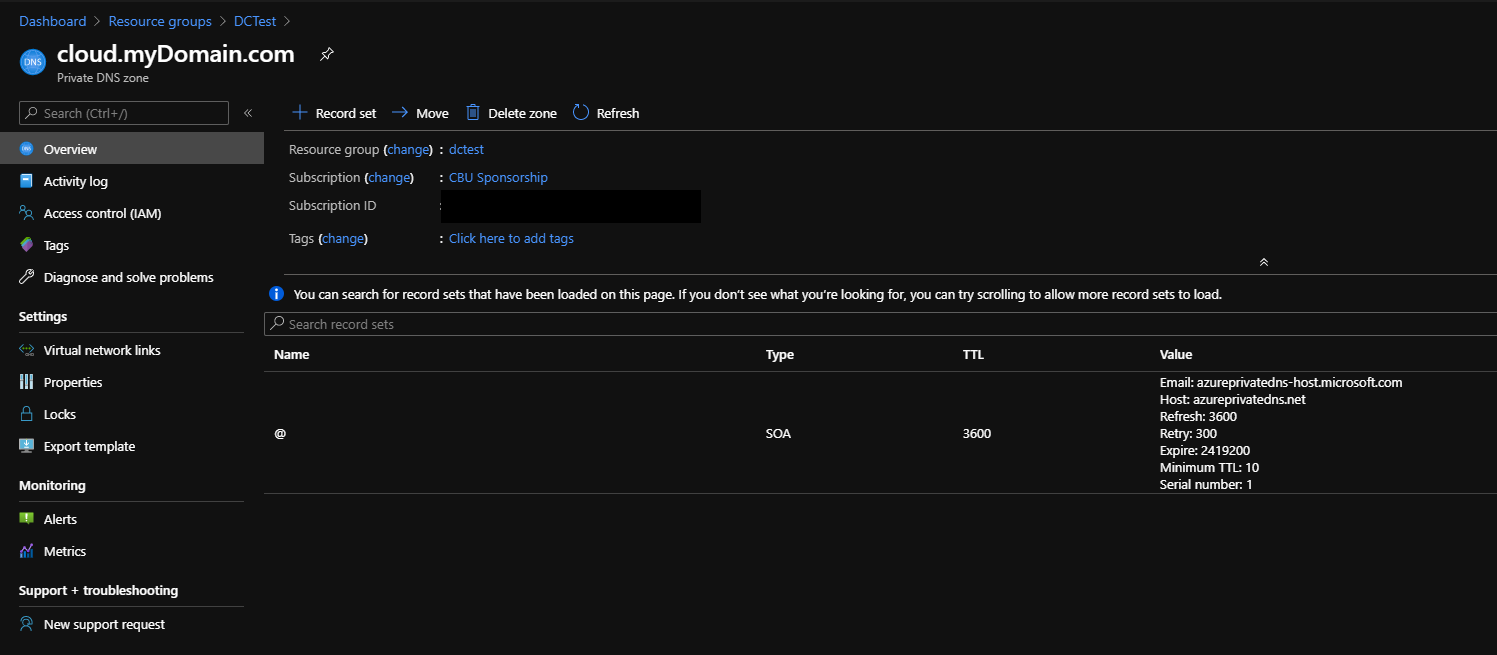
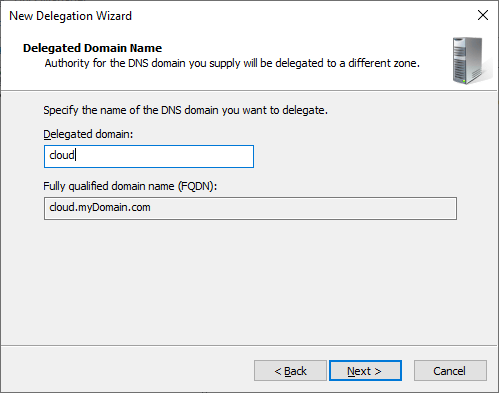
Simple: you have a local domain - myDomain.com - and you want to use a sub-domain - cloud.myDomain.com - for automation purposes in Azure.
Architecture
There are a few approaches you can take, but the simplest and most elegant is the following:
- DNS Delegation on your local DNS server for the sub-domain
- The Azure Private DNS Zone for the sub-domain
- A CoreDNS Instance running the Azure plugin
Setup
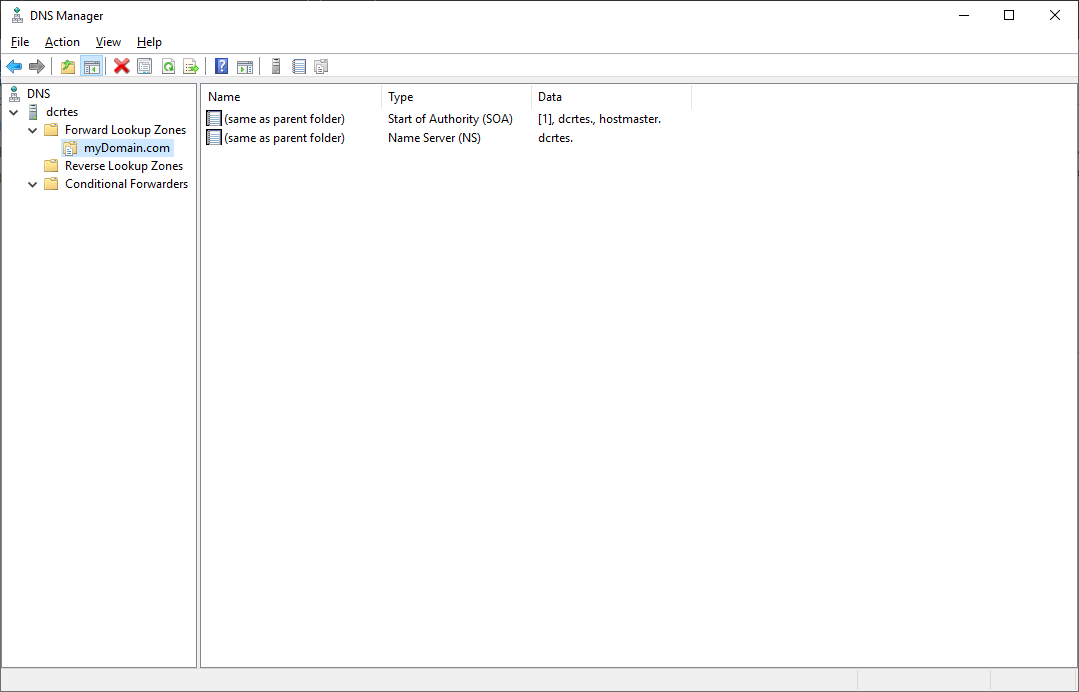
Local DNS Zone
It doesn’t really matter what DNS solution you use, as long as you can set up a DNS delegation. For this demo, I used a Microsoft DNS Server.
AKS Cluster
CoreDNS will be deployed to an AKS cluster, this one can be deployed using the following az cli commands:
1 | create service principal |
You can deploy an AKS cluster with a public or private facing master API. The example above deploys a public cluster, if you want to deploy it with a private endpoint, add the following parameter:
1 | --enable-private-cluster |
Do not assign owner permission for subscriptions that are used in production!
Azure Private DNS Zone
The following code lets you create the Azure Private DNS zone and link it to the AKS cluster VNET.
1 | Install-Module -Name Az.PrivateDns -Force |
CoreDNS on AKS
Now its time to deploy CoreDNS on the AKS cluster. To do this, you can use the deployment down below.
The .yaml file represents the configuration of CoreDNS - it consists of three Kubernetes objects:
- Service - used to expose the CoreDNS application with an Azure Load Balancer
- Config Map - the configuration of Core DNS
- Deployment - deployment of CoreDNS Pods
The .yaml file creates a config map which us used by CoreDNS to connect to Azure with the applied credentials for the specified DNS zone.
You can get more information about the Azure plugin for CoreDNS here.
1 | Config Map: |
In addition to the Azure plugin, we use the log, errors and cache plugins as well. This comes in handy for debugging and troubleshooting.
You might want to change the values of the deployment down below. You can use the same service principal for testing, but for production, you should limit the access to the DNS zone only.
1 |
|
The domain name must be all lower case in the config map! Otherwise the resolution will not work.
Connect to the AKS cluster:
1 | az login |
Afterwards, we can use kubectl to manage the cluster:
1 | kubectl create namespace dns |
You can check the result with:
1 | kubectl get pods -n dns |
And it should look like this:
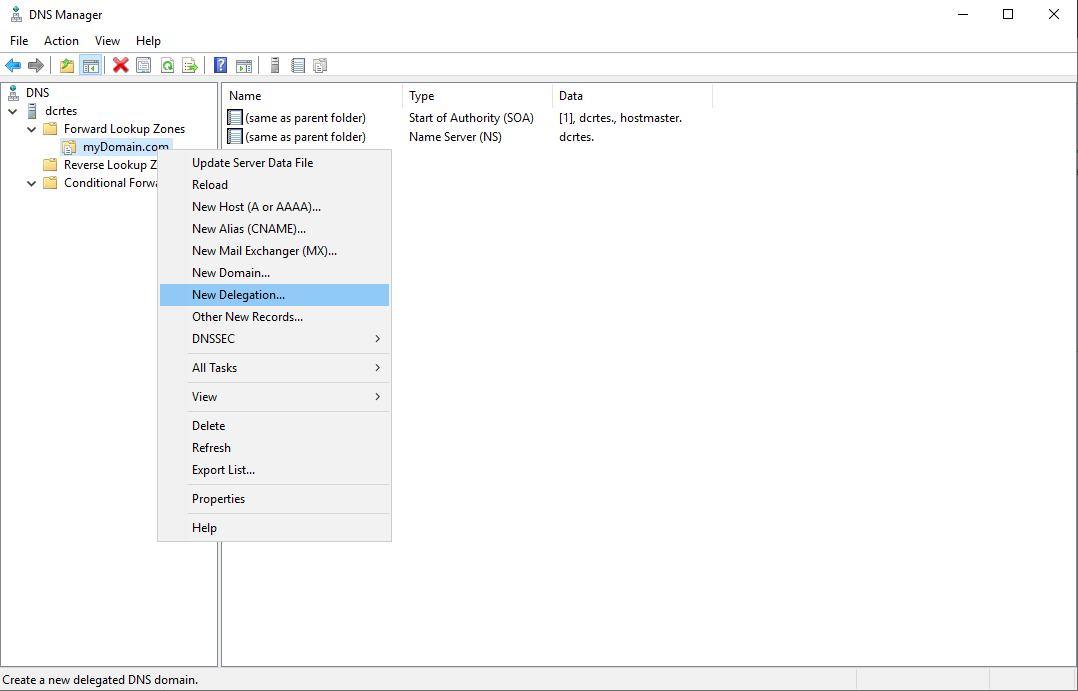
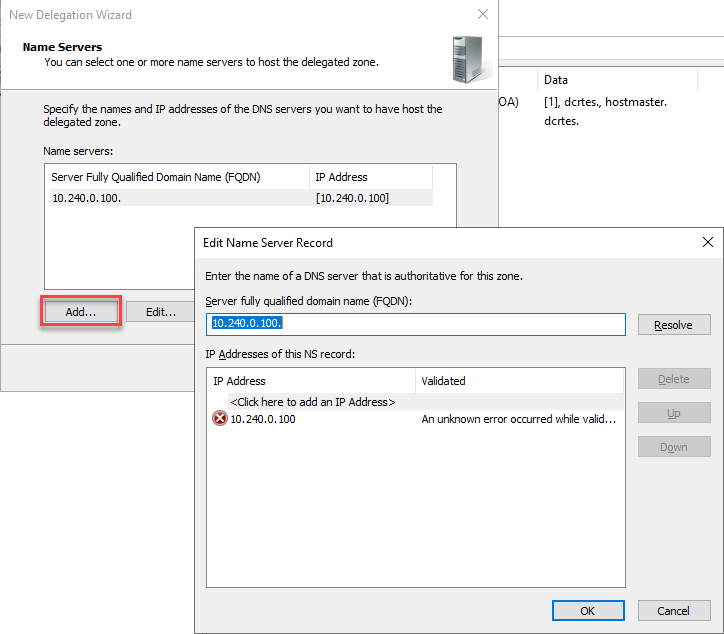
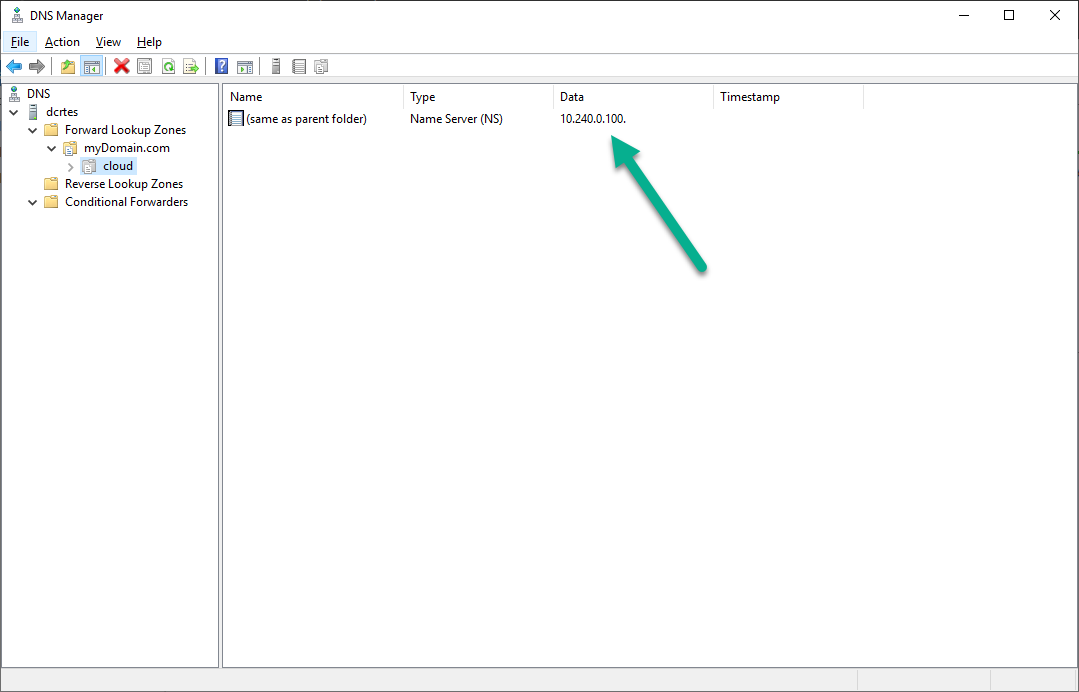
DNS Delegation
The last step is to set up the DNS delegation on the local DNS Server:
Testing
When setup is done, we can create a record in the zone:
1 | $RecordSet = New-AzPrivateDnsRecordSet -Name server1 -RecordType A -ResourceGroupName dctest -ZoneName 'cloud.mydomain.com' -Ttl 3600 |
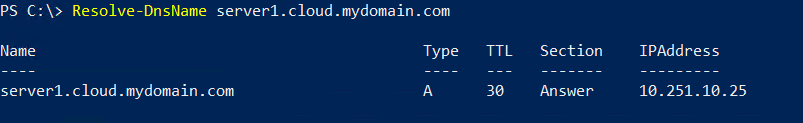
On the local DNS server, run the following command to check, if the resolution works:
1 | Resolve-DnsName -Name 'server1.cloud.mydomain.com' |
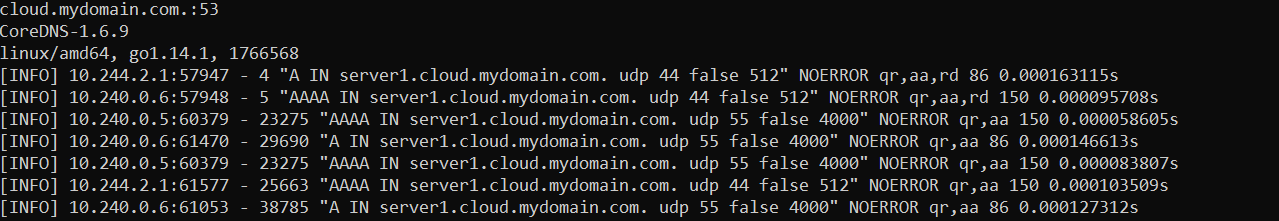
Check the CoreDNS logs:
1 | kubectl get pods -n dns |
Everything looks good 😎
Conclusion
Now you can resolve DNS names managed in a Azure Private DNS Zone from any client in your network, that uses the local DNS server.
I hope you liked the post, you can also checkout my first post about hybrid DNS on Azure here.