Entra ID Private Access – Enable traffic forwarding
In the last few months, Microsoft has made a lot of changes to Entra ID and added new features. One of them, which has come out of preview, is Microsoft Entra ID Private Access.
With Private Access, legacy VPNs are a thing of the past. Private Access not only allows web services to be published via the web application proxy using the Entra ID, as was previously the case, but now also dedicated resources or entire network segments using quick access.
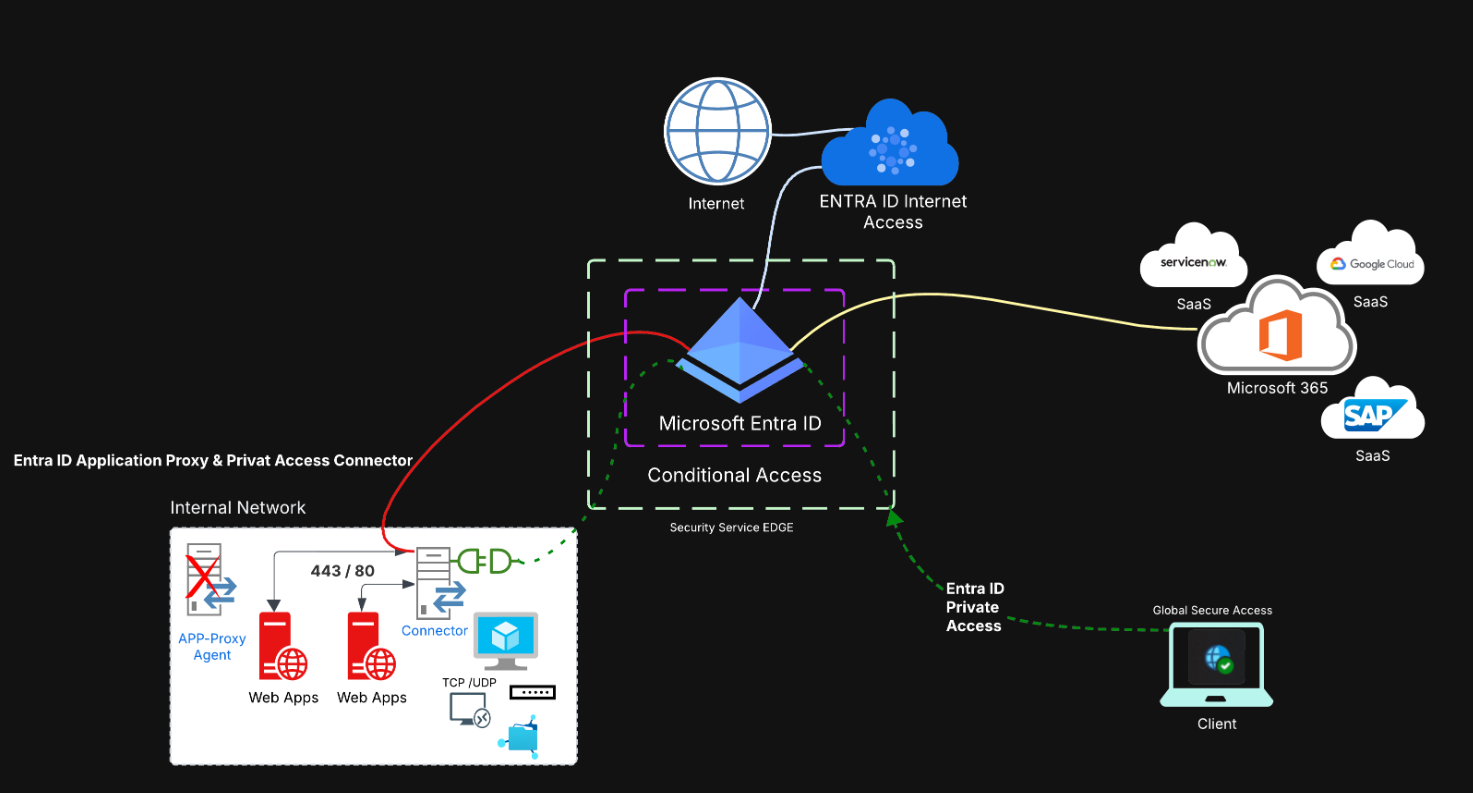
To activate the service, there are still a few issues. When you go to the portal (entra.microsoft.com) and click on ‘Global Secure Access’ and then ‘Activate’ under ‘Traffic’, you will see the status of the activated services after a while.
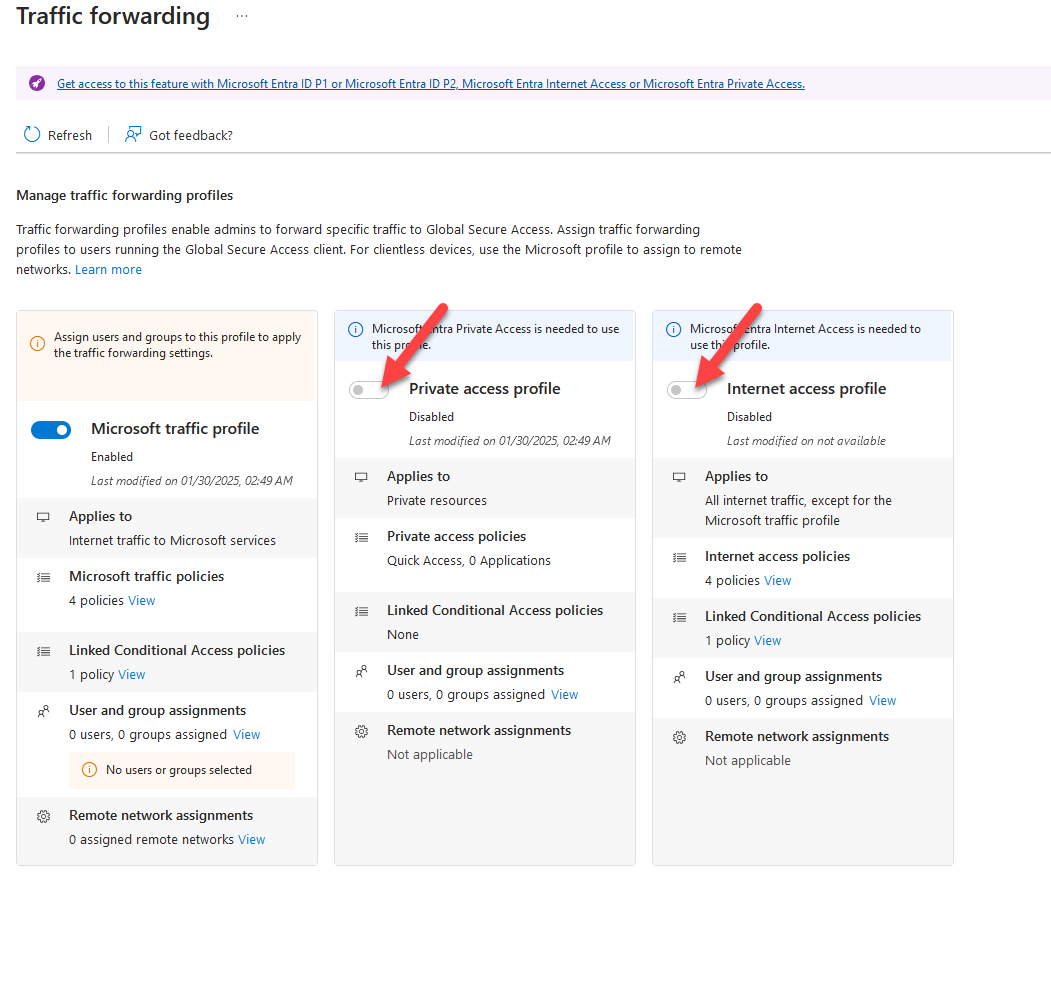
Best case scenario: you can simply activate the services using the toggle. However, this does not work for a large number of tenants and activations because Microsoft has a few problems in this context.
To still be able to use the service, you can check and adjust the status of Private Access using Graph.
To do this, we can use the following command to retrieve the status directly in the Graph Explorer:
https://graph.microsoft.com/beta/networkAccess/forwardingProfiles?
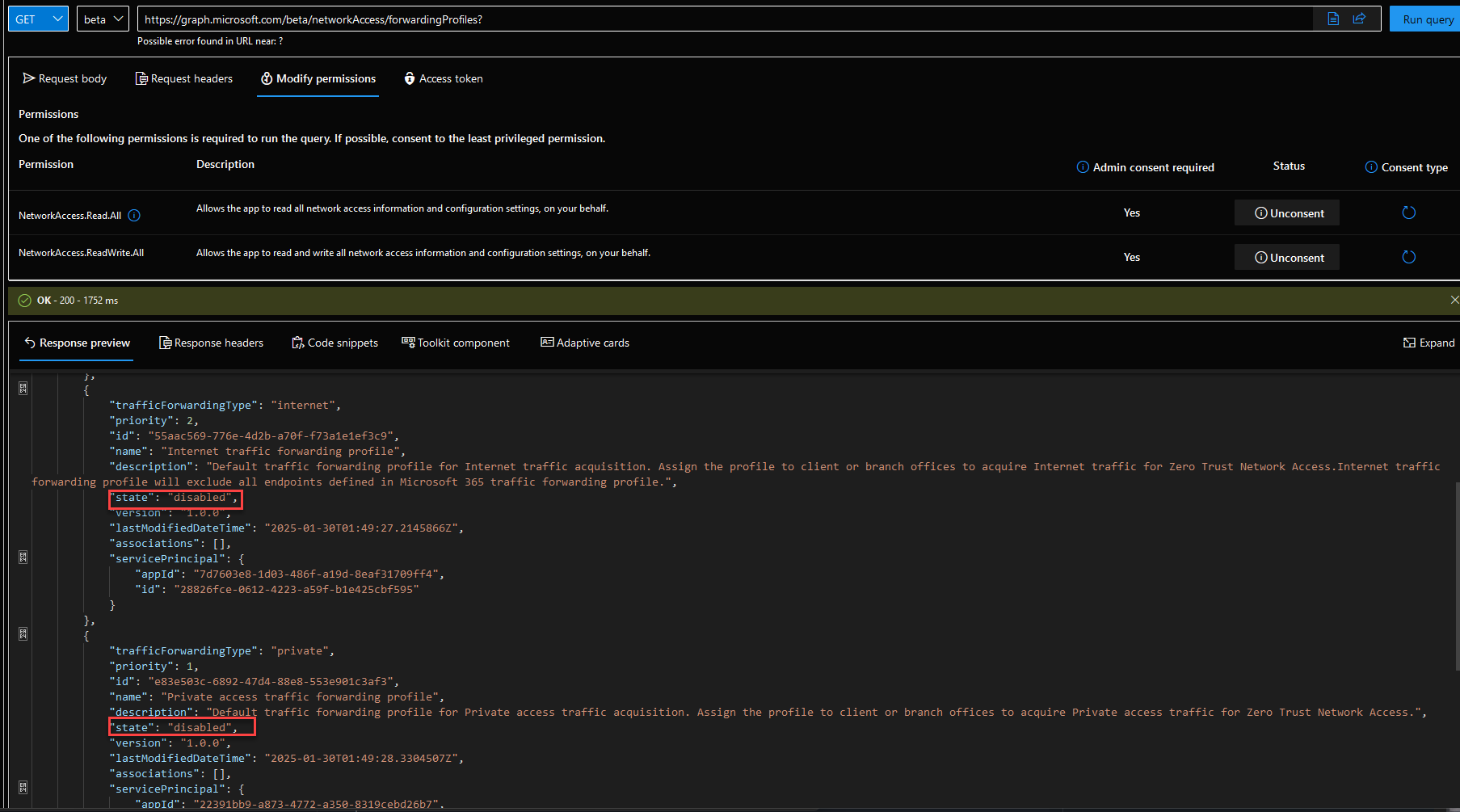
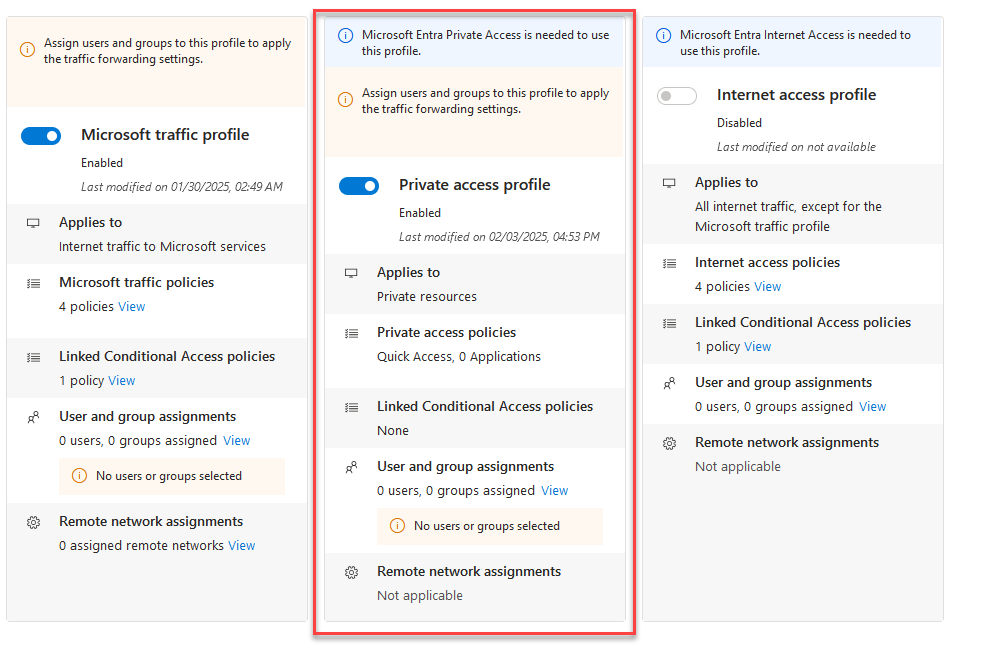
Depending on the profile, we can see in Status how the corresponding Service / Traffic forwarding Profile is configured and see that it is disabled, so we can now enable it in the 2nd step.
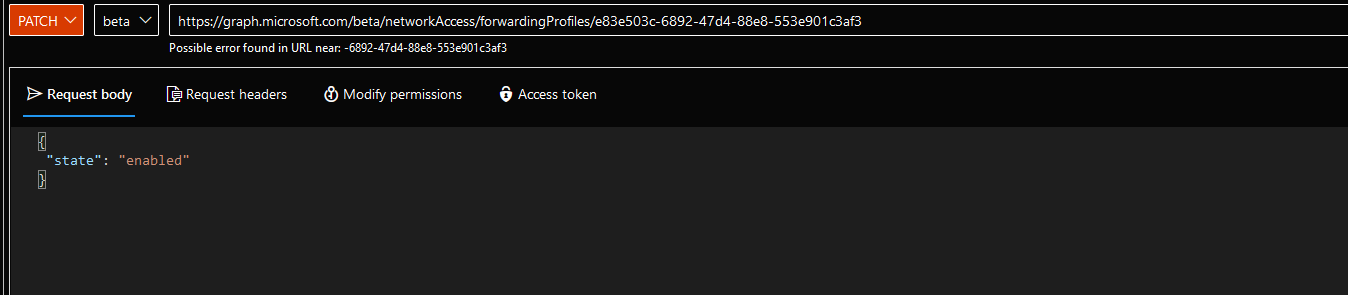
To do this, we apply a patch using Graph Explorer / API and enable the corresponding policy we want. To do this, we note / copy the ID of the profile from the previous step that we want to enable.
https://graph.microsoft.com/beta/networkAccess/forwardingProfiles/{id}
Furthermore, we are adding the following information to the request body:
{
"state": "enabled"
}
For example:
https://graph.microsoft.com/beta/networkAccess/forwardingProfiles/e83e503c-6892-47d4-8828-551901cas2f3
The following response should now come back. The respective Traffic forwarding Policy should now be enabled. This can also be seen directly in the Entra ID Portal.
Enable Wake-on-LAN (WOL) with PowerShell
With every recent Windows 10 update, and they happen a lot, Windows unfortunately also resets the power settings of the network adapters. Since I like to start both my PC and notebook from a remote location or from within the same network, I wrote a little PowerShell function to enable Wake-on-LAN (WoL) again.
Microsoft Findtime / Meeting Poll
I often have situations, where the scheduling of meetings is not done effectively. Tools like Doodle, mail or even phone calls are used to coordinate appointments even though Office 365 - including FindTime is available.\nTherefore, I would like to go over the integrated functionalities of Office 365 and FindTime again.
