AWS Root User Management for SSO using Azure Active Directory - Part 1
Using a central IAM provider is certainly a great thing. While setting SSO up for AWS, the management for the AWS root-users became an issue, because its required for them to have globally unique e-mail address. This might not a problem for small companies, but if you plan several hundred or even thousand of AWS-accounts, this becomes a nightmare real fast. In this post, I will go over one approach on how you can manage all your root-users with M365 offerings and some Azure services, pretty much for free.
Introduction
This is a multi part post - you can find all related posts here:
- Part 1 - Challenge, Architecture, next steps (You are here)
- Part 2 - Shared Mailboxes
- Part 3 - API
The Challenge
Depending on how your organization managing e-mail addresses, setting up and managing hundreds or even thousands of e-mail accounts can cause some major issues in your IT department. Most companies have a central e-mail solution and technical users have one purpose and one purpose only, even if they only used for sending mails.
Some possible problems:
- cost
- using e-mail in Azure AD accounts and something like G-Suite cost money for licenses to have a mailbox
- administrative overhead
- security concerns
- you have to disable 2FA for these accounts
- access to several mailboxes
- plenty more
Some obvious Challenge, or I would rather say inconveniences emerge regardless:
- MFA 2FA setup for AWS root-users
- storing and managing credentials
- managing e-mail addresses
The main goal of this series is to setup the management of centrally managed e-mail addresses for the root-users.
Looking at the AWS account structure (below), you will see, that each AWS account, even the root account, requires a root user.
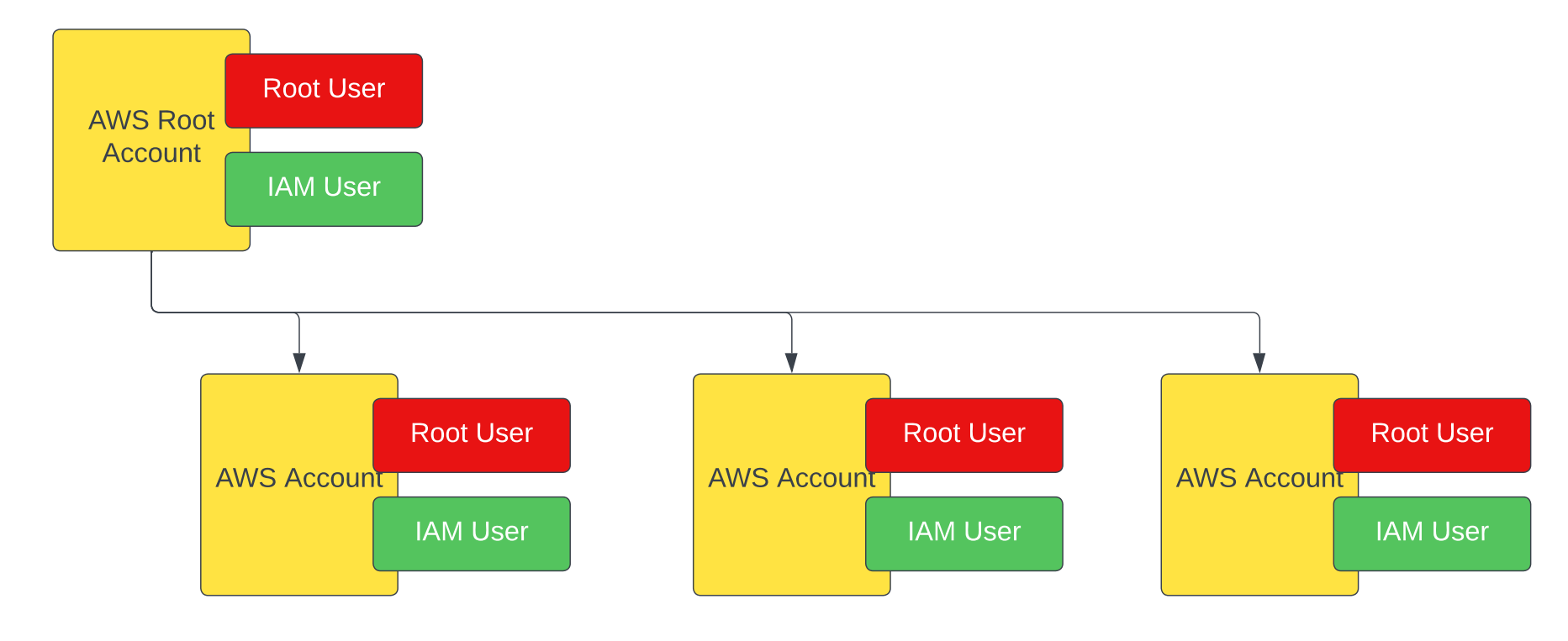
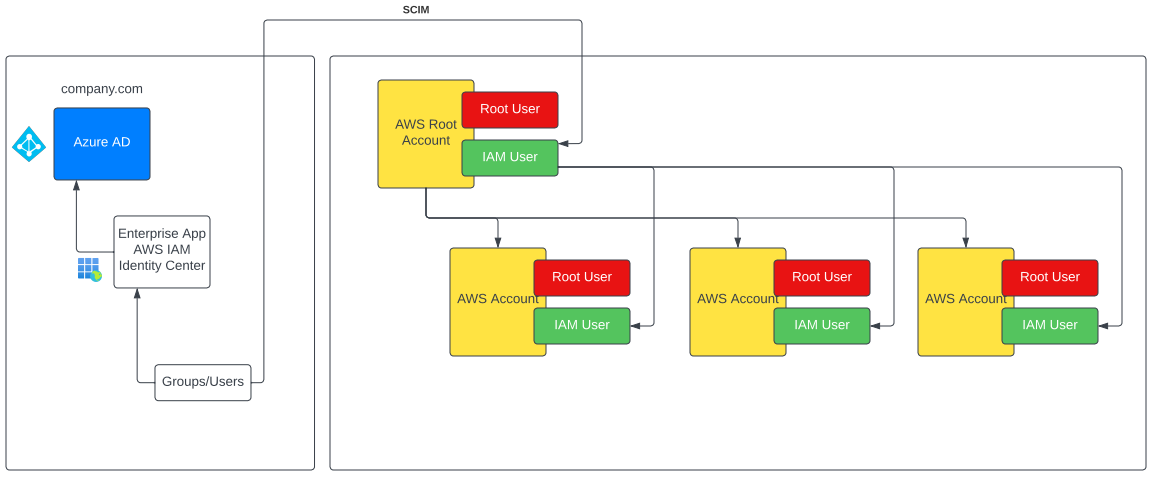
On the other hand, IAM users must not be unique and also can be created using SCIM from your central identity provider (an Azure AD for instance). They can even be created by SCIM as IAM users in the AWS root account and then be added as IAM Users to child AWS accounts. The diagram below shows this
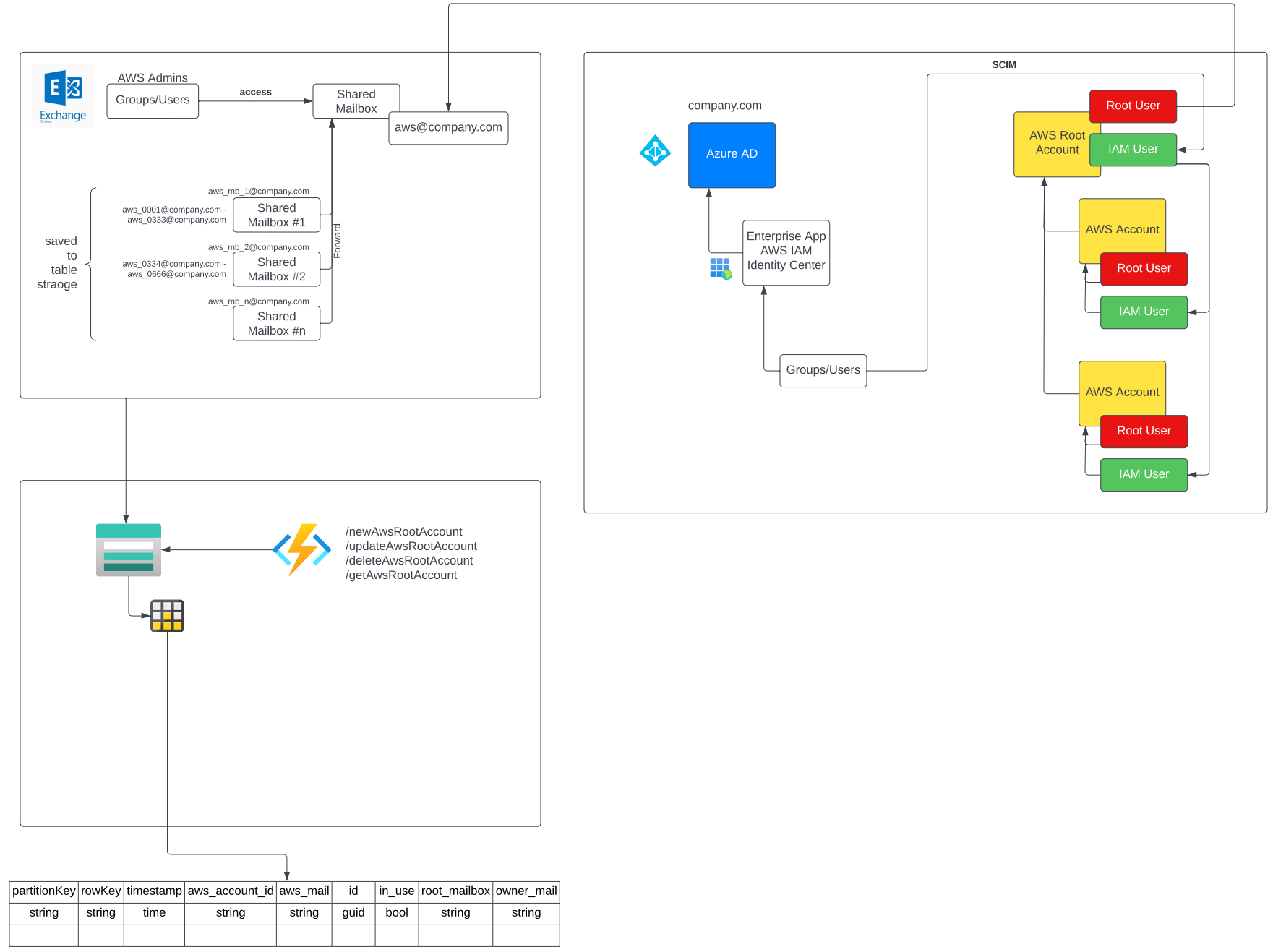
Architecture
The solution has three main components:
- Shared Mailboxes from Exchange Online
- a database for managing the shared mailboxes and their aliases
- a Function App to provide an API for the AWS DevOps team
The figure below shows the architecture but I will cover all of the components in the next two posts.
Automatically generate PowerShell Markdown documentation - Part 1
This blog series introduces a PowerShell module that automatically generated MarkDown documentation of your PowerShell Scripts and modules. It also gives an introduction into Abstract Syntax Trees (ASTs) in PowerShell.
AWS Root User Management for SSO using Azure Active Directory - Part 2
Using a central IAM provider is certainly a great thing. While setting SSO up for AWS, the management for the AWS root-users became a issue, because its required for them to have globally unique e-mail address. This might not a problem for small companies, but if you plan several hundred or even thousand of AWS-accounts, this becomes a nightmare real fast. In this post, I will go over one approach on how you can manage all your root-users with M365 offerings and some Azure services, pretty much for free. This is the second part of the series, that covers the Shared Mailbox Setup.
