

Power Automate, Microsoft 365
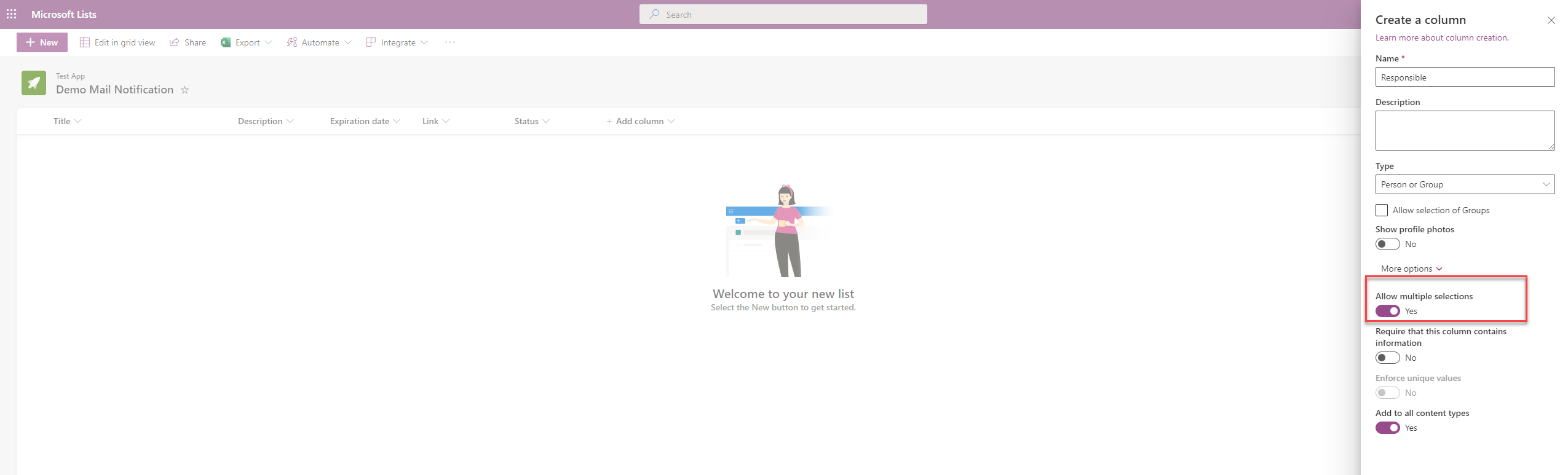
Send Email Notification with Power Automate based on SharePoint List Multi-Select Person Field
Many automations with Power Automate are based on SharePoint lists. Some of them are used to collect, analyze data and send notifications. This is where most of the requests come to send notifications by mail to specific users. \nThis brings us directly to the topic of sending messages via Outlook Connector based on a person (with multiselect) field within the SharePoint list.
SharePoint Online
Import Excel in SharePoint & Microsoft 365 Lists
In many cases, the use of Microsoft 365 Services requires existing processes & workflows to be reworked and existing Microsoft Excel lists to be replaced by Power Apps and SharePoint Online Lists / Microsoft Lists, because with the integration into the native Office 365 environment, new and significant possibilities for automation are provided and previously time-consuming processes can be accelerated.
Office 365
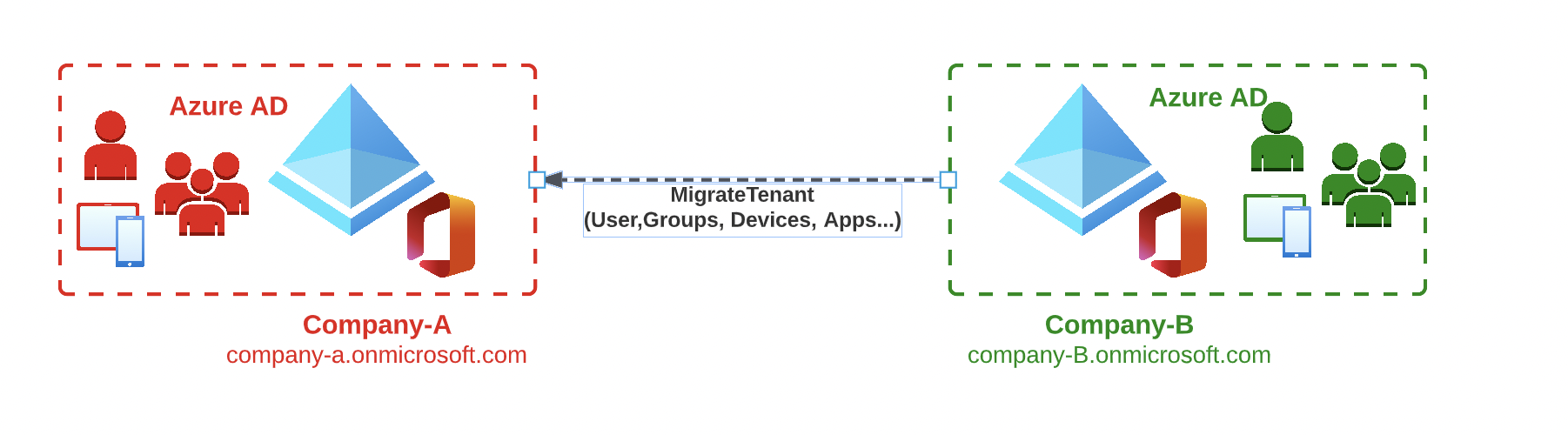
Office 365 Tenant to Tenant Migration Identity Planning Part 2
In the first part of the blog series, we took a look at the topic of planning and selecting the migration scenario and developed a long-term strategy based on the business and technical requirements and defined how the tenant migration should be implemented schematically.

AzureAD, Microsoft Graph API
Graph API - Remove Azure AD Group Member
Many tasks and processes can be automated quickly and easily using the Microsoft Graph API. This can be implemented with low-code applications such as Logic App or, for example, via Azure Function and PowerShell. Depending on the requirements, complexity, a variety of options are available.

Azure - GitHub - Continuous Integration
Start/Stop AKS and ADX Clusters with GitHub Actions and Azure Pipelines
Azure Kubernetes Services (AKS) and Azure Data Explorer (ADX) clusters are SaaS offerings based on virtual machines. It is probably the oldest way to safe money in the cloud - just turn them off when you do not need them - here are two ways to do this.
